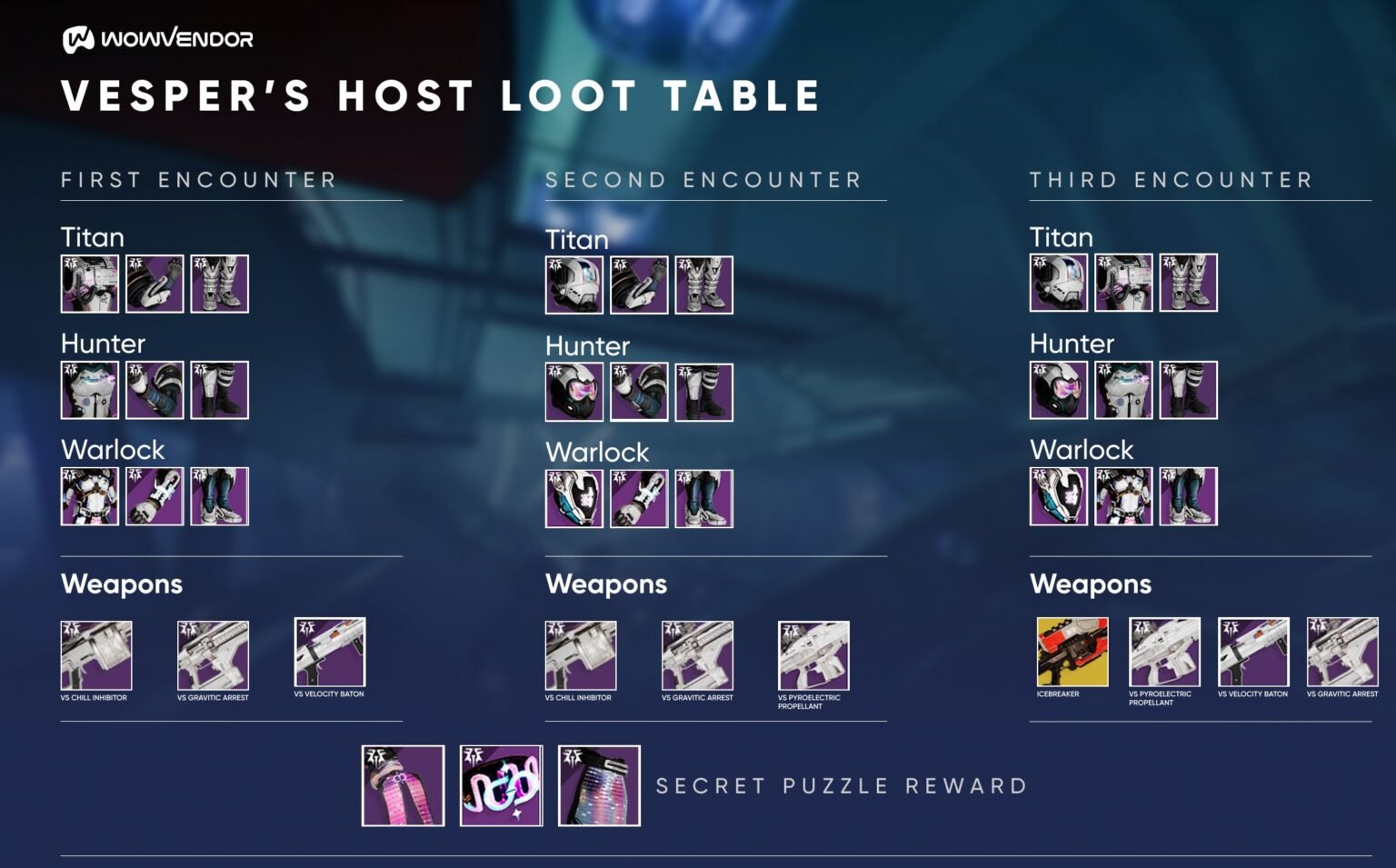
DBOA: Understanding the Role of Data Breach Omnibus Agreements in Cybersecurity
DBOA: Understanding the Role of Data Breach Omnibus Agreements in Cybersecurity In today’s digital landscape, data breaches are an ever-present threat to organizations of all sizes. The potential financial, reputational, and legal consequences of a data breach can be devastating. To mitigate these risks, organizations are increasingly turning to various cybersecurity measures, including the use … Read more